Lab 1 - Exercise 3 - Create and manage sensitivity labels
Joni Sherman, an Information Security Administrator at Contoso Ltd., is deploying a modern sensitivity labeling framework to strengthen data protection across the organization. She’ll create and publish sensitivity label groups and labels to classify and protect content, including encryption, auto-labeling, and Double Key Encryption (DKE). Joni will also integrate Microsoft Purview with Microsoft Defender for Cloud Apps to extend data protection controls to files stored in cloud locations.
Tasks:
- Enable support for sensitivity labels
- Create a label group
- Create a child label
- Publish labels
- Configure auto-labeling
- Create and publish a DKE label for confidential content
- Enable Microsoft Purview integration in Defender for Cloud Apps
- Create a file policy to label externally shared files
Estimated time: 60-90 minutes
Task 1 – Enable support for sensitivity labels
In this task, you’ll enable co-authoring for sensitivity labels, which also enables sensitivity labels for files in SharePoint and OneDrive.
-
You should still be logged into Client 1 VM (SC-401-CL1) as the SC-401-CL1\admin account and logged into Microsoft Purview as Joni Sherman.
-
Open Microsoft Edge, then navigate to
https://purview.microsoft.com. -
In the left navigation, select Settings > Information Protection.
-
On the Information Protection settings page, ensure you’re on the Co-authoring for files with sensitivity labels tab.
-
Select the checkbox for Turn on co-authoring for files with sensitivity labels.
-
Select Apply at the bottom of the screen.
You have successfully enabled support for sensitivity labels for files in SharePoint and OneDrive.
Task 2 – Create a label group
In this task, you’ll create a label group to organize internal sensitivity labels. Label groups act as containers for related labels, like department or business unit classifications.
-
You should still be logged into Client 1 VM (SC-401-CL1) as the SC-401-CL1\admin account.
-
In Microsoft Edge, navigate to
https://purview.microsoft.com. -
In the Microsoft Purview portal, select Solutions from the left sidebar, then select Information Protection.
-
On the Microsoft Information Protection page, on the left sidebar, select Sensitivity labels.
-
On the Sensitivity labels page select + Create > Label group.
-
The New label group configuration will start. On the Provide basic details for this label group, enter:
- Name:
Internal - Display name:
Internal - Description for users:
Internal sensitivity label. - Description for admins:
Internal sensitivity label group for Contoso.
- Name:
-
Select Next.
-
On the Review your settings and finish page, select Create label group.
-
On the Your label group was created successfully page, select Don’t create a label yet, then select Done.
You’ve created a label group for internal use. This group helps you manage related labels for specific departments or data categories.
Task 3 – Create a child label
Now that you’ve created a label group, you’ll add a child label for HR-related content. This label enforces encryption and content markings to protect HR data from unauthorized access.
-
On the Sensitivity labels page, find the Internal sensitivity label group. Select the vertical ellipsis (…) next to it, then select + Create label in group from the dropdown menu.
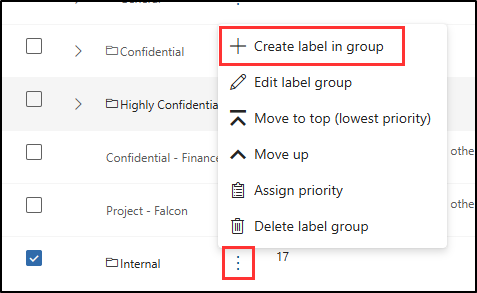
-
The New sensitivity label wizard will start. On the Provide basic details for this label page enter:
- Name:
Employee data (HR) - Display name:
Employee data (HR) - Description for users:
This HR label is the default label for all specified documents in the HR Department. - Description for admins:
This label is created in consultation with Ms. Jones (Head of the HR department). Contact her if you need to change the label settings.
- Name:
-
Select Next.
-
On the Define the scope for this label page, select Files and Emails. If the checkbox for Meetings is selected, make sure it’s deselected.
-
Select Next.
-
On the Choose protection settings for labeled items page, select the Control access and Apply content marking options, then select Next.
-
On the Access control page, select Configure access control settings.
-
Configure the encryption settings with these options:
- Assign permissions now or let users decide?: Assign permissions now
- User access to content expires: Never
- Allow offline access: Only for a number of days
- Users have offline access to the content for this many days: 15
- Select the Assign permissions link. On the Assign permissions flyout panel, select + Add any authenticated users, then select Save to apply this setting.
-
On the Access control page, select Next.
-
On the Content marking page, select the toggle to enable Content marking.
-
For each of the following marking types, select the checkbox, then select the edit icon to enter the text:
Marking type Text Add a watermark INTERNAL USE ONLYAdd a header Internal DocumentAdd a footer Contoso Confidential -
Select Next.
-
On the Auto-labeling for files and emails page, select Next.
-
On the Define protection settings for groups and sites page, select Next.
-
On the Review your settings and finish page, select Create label.
-
On the Your sensitivity label was created page, select Don’t create a policy yet, then select Done.
You’ve created a child label within the Internal label group. The label applies encryption and content markings to HR documents, making sensitive data easy to identify and protected by policy.
Task 4 – Publish labels
Next, you’ll publish the HR label from the Internal label group so users in the HR department can apply it to their documents.
-
You should still be logged into Client 1 VM (SC-401-CL1) as the SC-401-cl1\admin account, and you should be logged into Microsoft Purview as Joni Sherman.
-
In Microsoft Edge, the Microsoft Purview portal tab should still be open. If not, navigate to
https://purview.microsoft.com> Solutions > Information Protection > Sensitivity labels. -
On the Sensitivity labels page select Publish labels.
-
The publish sensitivity labels configuration will start.
-
On the Choose sensitivity labels to publish page, select the Choose sensitivity labels to publish link.
-
On the Sensitivity labels to publish flyout panel, select the Internal/Employee data (HR) checkbox, then select Add at the bottom of the flyout page.
-
Back on the Choose sensitivity labels to publish page, select Next.
-
On the Assign admin units page, select Next
-
On the Publish to users and groups page, select Next.
-
On the Policy settings page, select Next.
-
On the Default settings for documents select Next.
-
On the Default settings for emails select Next.
-
On the Default settings for meetings and calendar events select Next.
-
On the Default settings for Fabric and Power BI content page, select Next.
-
On the Name your policy page, enter:
-
Name:
Internal HR employee data -
Enter a description for your sensitivity label policy:
This HR label is to be applied to internal HR employee data.
-
-
Select Next.
-
On the Review and finish page, select Submit.
-
On the New policy created page, select Done to finish publishing your label policy.
You’ve published the Internal label group and its HR label so users can apply them to HR documents. It might take up to 24 hours for the policy to propagate across services.
Task 5 – Configure auto-labeling
You’ll now create a child label for financial data and configure it to apply automatically to content containing financial identifiers such as credit card or bank routing numbers.
-
You should still be logged into Client 1 VM (SC-401-CL1) as the SC-401-cl1\admin account.
-
In Microsoft Edge, navigate to
https://purview.microsoft.comand log into the Microsoft Purview portal as Joni Sherman. -
In the Microsoft Purview portal, select Solutions > Information Protection > Sensitivity labels.
-
On the Sensitivity labels page, find the Internal sensitivity label. Select the vertical ellipsis (…), then select + Create label in group from the dropdown menu.
-
On the Provide basic details for this label page, enter:
Details Text Name Financial DataDisplay name Financial DataDescription for users This content contains financial data that must be labeled and protected.Description for admins This label is used for content that includes sensitive financial identifiers. -
Select Next.
-
On the Define the scope for this label page, select Files and Emails. If the checkbox for Meetings is selected, make sure it’s deselected.
-
Select Next.
-
On the Choose protection settings for labeled items page, select Next.
-
On the Auto-labeling for files and emails page, set the Auto-labeling for files and emails to enabled.
-
In the Detect content that matches these conditions section, select + Add condition > Content contains.
-
In the Content contains section, select the Add > Sensitive info types.
-
In the Sensitive info types flyout page, search for and select these sensitive info types:
Credit Card NumberABA Routing NumberSWIFT Code
-
Select Add.
-
Back on the Auto-labeling for files and emails page, select Next.
-
On the Define protection settings for groups and sites page, select Next.
-
On the Review your settings and finish page, select Create label.
-
On the Your sensitivity label was created page, select Automatically apply label to sensitive content, then select Done.
-
On the Create auto-labeling policy flyout page, select Review policy.
-
On the Name your auto-labeling policy page, leave the default, then select Next.
-
On the Choose a label to auto-apply page, review to ensure the Internal/Financial Data label is selected, then select Next.
-
On the Assign admin units page, select Next.
-
On the Choose locations where you want to apply the label page, select the options for:
- Exchange email
- SharePoint sites
- OneDrive accounts
-
Select Next.
-
On the Set up common or advanced rules page, leave the default Common rules selected, then select Next.
-
On the Define rules for content in all locations page, expand the rules for Financial Data rule to ensure the expected rules are defined, then select Next.
-
On the Additional settings for email page, select Next.
-
On the Decide if you want to test out the policy now or later page, select Run policy in simulation mode, and select the checkbox for Automatically turn on policy if not modified after 7 days in simulation.
-
Select Next.
-
On the Review and finish page, select Create policy.
-
On the Your auto-labeling policy was created page, select Done.
You’ve created a child label for financial data and configured an auto-labeling policy that detects and labels content containing financial information.
Task 6 – Create and publish a DKE label for confidential content
Next, you’ll create a child label in the Internal group that uses Double Key Encryption (DKE) and dynamic watermarking to protect confidential legal content.
-
You should still be logged into Client 1 VM (SC-401-CL1) as the SC-401-cl1\admin account.
-
In Microsoft Edge, navigate to
https://purview.microsoft.comand log into the Microsoft Purview portal as Joni Sherman. -
In the Microsoft Purview portal, select Solutions > Information Protection > Sensitivity labels.
-
On the Sensitivity labels page, find the Internal sensitivity label group. Select the vertical ellipsis (…), then select + Create label in group from the dropdown menu.
-
On the Provide basic details for this label page, enter:
Details Text Name Confidential LegalDisplay name Confidential LegalDescription for users Use this label for highly sensitive legal content that must be encrypted using Double Key Encryption.Description for admins Label configured with DKE and dynamic watermarking for highly sensitive legal content. -
Select Next.
-
On the Define the scope for this label page, select Files and Emails. If the checkbox for Meetings is selected, make sure it’s deselected.
-
On the Choose protection settings for the types of items you selected page, select Control access, then select Next.
-
On the Access control page, select Configure access control settings.
-
Configure the encryption settings with these options:
-
Assign permissions now or let users decide?: Assign permissions now
-
User access to content expires: A number of days after label is applied
-
Access expires this many days after the label is applied: 5
-
Allow offline access: Never
-
Select the Assign permissions link. On the Assign permissions flyout panel, select the + Add users or groups.
-
On the Add users or groups flyout page, search for and select
Legal TeamandJoni Sherman, and select Add. -
On the Assign permissions page, select Save.
-
-
Back on the Access control page, select the checkbox for Use dynamic watermarking, then select Customize text (optional).
-
On the Add custom text to watermark (optional) page, enter
Confidential, then select UPN and Timestamp. -
Select Save at the bottom of the flyout page.
-
Back on the Access control page, select the checkbox for Use Double Key Encryption, and enter
https://testingdke1.azurewebsites.net/Testas the URL for the Double Key Encryption service. -
Select Next.
-
On the Auto-labeling for files and emails page, select Next.
-
On the Define protection settings for groups and sites page, select Next.
-
On the Review your settings and finish page, select Create label.
-
On the Your sensitivity label was created page, select Publish label to users’ apps, then select Done.
-
On the Publish label flyout page, select Create new label policy.
-
On the Choose sensitivity labels to publish page, select Choose sensitivity labels to publish and add the Internal/Confidential Legal label, then select Add.
-
Select Next.
-
On the Assign admin units page, select Next.
-
On the Publish to users and groups page, leave the default selected, then select Next.
-
On the Policy settings page, select the checkbox for Users must provide a justification to remove a label or lower its classification, then select Next.
-
On the Default settings for documents page, select Next.
-
On the Default settings for emails page, select Next.
-
On the Default settings for meetings and calendar events page, select Next.
-
On the Default settings for Fabric and Power BI content page, select Next.
-
On the Name your policy page, enter:
-
Name:
Confidential Legal -
Description:
Enables manual use of the DKE label for confidential content accessible by Legal.
-
-
Select Next.
-
On the Review and finish page, select Submit.
-
On the New policy created page, select Done.
You’ve created and published a child label using Double Key Encryption and dynamic watermarking. This label restricts access to authorized users and enforces justification for downgrading classifications.
Task 7 – Enable Microsoft Purview integration in Defender for Cloud Apps
With your sensitivity labels created and published, you’ll now integrate Microsoft Purview with Microsoft Defender for Cloud Apps. This integration allows Defender to scan files for sensitivity labels and apply file monitoring.
-
You should still be logged into Client 1 VM (SC-401-CL1) as the SC-401-CL1\admin, and you should still be logged in as Joni Sherman.
-
Open Microsoft Edge, then go to Microsoft Defender by navigating to
https://security.microsoft.com. -
In the left navigation, select Settings, then select Cloud Apps.
-
Under the Information Protection section in the left pane, select Microsoft Information Protection.
-
On the Microsoft Information Protection page, select both checkboxes available on the page.
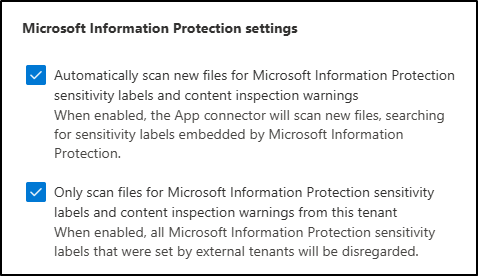
-
Automatically scan new files for Microsoft Information Protection sensitivity labels and content inspection warnings
Enables Defender for Cloud Apps to automatically scan new or modified files for sensitivity labels and content inspection warnings from Microsoft Purview.
-
Only scan files for Microsoft Information Protection sensitivity labels and content inspection warnings from this tenant
Limits scanning to labels and warnings created in your own organization. Labels applied by external tenants will be ignored.
-
-
Select Save to apply the settings.
-
Under the Information Protection section in the left pane, select Files.
-
On the Files page, select Enable file monitoring.
-
Select Save to apply the settings.
You’ve enabled Microsoft Purview integration in Defender for Cloud Apps. Defender can now detect sensitivity labels and monitor files for policy evaluation and governance actions.
Task 8 – Create a file policy to label externally shared files
Finally, you’ll create a file policy that automatically applies a sensitivity label to files shared externally. This ensures sensitive content remains protected even when shared outside the organization.
-
In Microsoft Defender, navigate to Cloud apps > Policies > Policy management.
-
Select the Information protection tab, then select Create policy > File policy.
-
On the Create file policy page, configure:
-
Policy name:
Auto-label externally shared files -
Policy severity: High
-
Category: DLP
-
In the Files matching all of the following section:
-
For the first filter, configure the dropdowns to: Access level equals external
-
For the second filter, configure the dropdowns to: Last modified after (date) and use today’s date
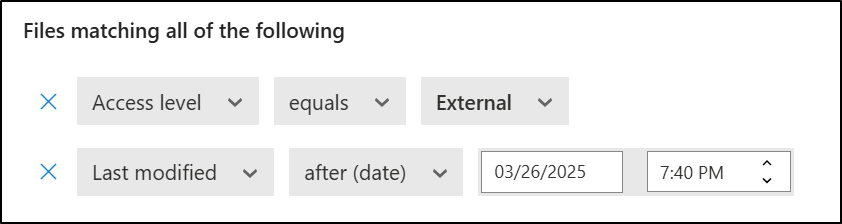
-
-
Under Governance actions, expand Microsoft OneDrive for Business:
-
Select the checkbox for Apply sensitivity label
-
In the dropdown select Highly Confidential-Specified People
-
-
Repeat the same process for Microsoft SharePoint Online
-
Select the checkbox for Apply sensitivity label
-
Select Highly Confidential-Specified People from the dropdown
-
-
-
Select Create to finish creating the file policy.
You’ve created a file policy that applies sensitivity labels to externally shared files. This policy extends your information protection strategy to cloud-stored content.