WWL Tenants - Terms of use
If you are being provided with a tenant as a part of an instructor-led training delivery, please note that the tenant is made available for the purpose of supporting the hands-on labs in the instructor-led training.
Tenants should not be shared or used for purposes outside of hands-on labs. The tenant used in this course is a trial tenant and cannot be used or accessed after the class is over and are not eligible for extension.
Tenants must not be converted to a paid subscription. Tenants obtained as a part of this course remain the property of Microsoft Corporation and we reserve the right to obtain access and repossess at any time.
Lab setup - Prepare your environment for administration
In this lab, you’ll configure and prepare your environment for administration tasks. You’ll enable required features, configure permissions, and prepare core services for administration.
Tasks:
- Enable Audit in the Microsoft Purview portal
- Enable device onboarding
- Enable insider risk analytics and data sharing
- Initialize Microsoft Defender XDR
- Configure multi-factor authentication in Microsoft Entra
Estimated time: 30-45 minutes
Task 1 - Enable Audit in the Microsoft Purview portal
In this task, you’ll enable Audit in the Microsoft Purview portal to monitor portal activities.
-
Log into Client 1 VM (SC-401-CL1) with the Admin account.
-
Open Microsoft Edge.
-
In Microsoft Edge, navigate to
https://purview.microsoft.comand sign in as MOD Administrator,admin@WWLxZZZZZZ.onmicrosoft.com(where ZZZZZZ is your unique tenant prefix provided by your lab hosting provider). Admin’s password should be provided by your lab hosting provider. -
In Microsoft Edge, navigate to the Microsoft Purview portal,
https://purview.microsoft.com, and log in. -
A message about the new Microsoft Purview portal will appear on the screen. Select Get started to access the new portal.

-
Select Solutions from the left sidebar, then select Audit.
-
On the Search page, select the Start recording user and admin activity bar to enable audit logging.
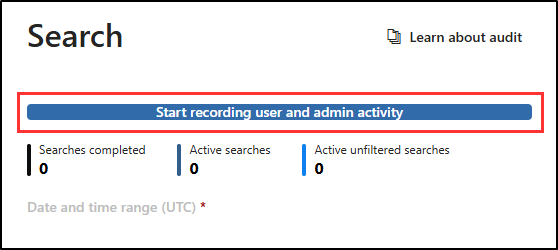
-
Once you select this option, the blue bar should disappear from this page.
[!Note] Note: If the Audit button doesn’t enable logging
In some tenants, selecting Start recording user and admin activity might not activate Audit.
If this happens, you can enable Audit through PowerShell instead:
-
Open an elevated Terminal window by right-clicking the Windows button and selecting Terminal (Admin).
-
Install the latest Exchange Online PowerShell module:
Install-Module ExchangeOnlineManagementConfirm any prompts by typing Y for Yes and pressing Enter.
-
Run the following command to change your execution policy:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope CurrentUser -
Close the elevated Terminal window and open a regular PowerShell session.
-
Connect to Exchange Online:
Connect-ExchangeOnlineSign in as
admin@WWLxZZZZZZ.onmicrosoft.com(where ZZZZZZ is your unique tenant prefix provided by your lab hosting provider). Admin’s password should be provided by your lab hosting provider. -
Check if Audit is enabled:
Get-AdminAuditLogConfig | FL UnifiedAuditLogIngestionEnabledIf it returns False, enable Audit:
Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $true -
Verify that it’s now enabled:
Get-AdminAuditLogConfig | FL UnifiedAuditLogIngestionEnabledThe command should return True once Audit is active.
-
You have successfully enabled auditing in Microsoft 365.
Task 2 – Enable device onboarding
In this task, you’ll enable device onboarding for your organization.
-
You should still be logged into Client 1 VM (SC-401-CL1) as the SC-401-CL1\admin account and logged in as the MOD Administrator in Microsoft Purview.
-
Select Settings from the left sidebar, then expand Device onboarding.
-
On the Device onboarding page, select Devices.
-
On the Devices page, select Turn on device onboarding then select Ok to confirm.
-
When prompted, select OK to confirm that device monitoring is being turned on.
You have now enabled device onboarding and can start to onboard devices to be protected with Endpoint DLP policies. The process of enabling the feature might take up to 30 minutes.
Task 3 – Enable insider risk analytics and data sharing
In this task, you’ll enable analytics and data sharing for Insider Risk Management.
-
You should still be logged into Client 1 VM (SC-401-CL1) as the SC-401-CL1\admin account and logged in as the MOD Administrator in Microsoft Purview.
-
In Microsoft Purview, navigate to Settings > Insider Risk Management > Analytics.
-
Toggle these settings to On:
-
Show insights at tenant level
-
Show insights at user level
-
-
Select Save at the bottom of the page.
-
Select Data sharing on the left navigation pane.
-
In the Data sharing section, toggle Share user risk details with other security solutions to On.
-
Select Save at the bottom of the page.
You have enabled analytics and data sharing for Insider Risk Management.
Task 4 – Initialize Microsoft Defender XDR
In this task, you’ll go to Microsoft Defender and wait for Microsoft Defender XDR to initialize.
-
You should still be logged into Client 1 VM (SC-401-CL1) as the SC-401-CL1\admin account and logged in as the MOD Administrator in Microsoft Purview.
-
In Microsoft Edge, navigate to
https://security.microsoft.com/to open Microsoft Defender. -
From the navigation pane, select Investigation & response > Incidents & alerts > Incidents.
[!Note] Note: Microsoft Defender XDR initialization
The Microsoft Defender XDR initialization screen might or might not appear depending on your lab tenant.
-
You’ll see a message stating that Microsoft Defender XDR is being prepared. This process runs automatically and might take a few minutes.
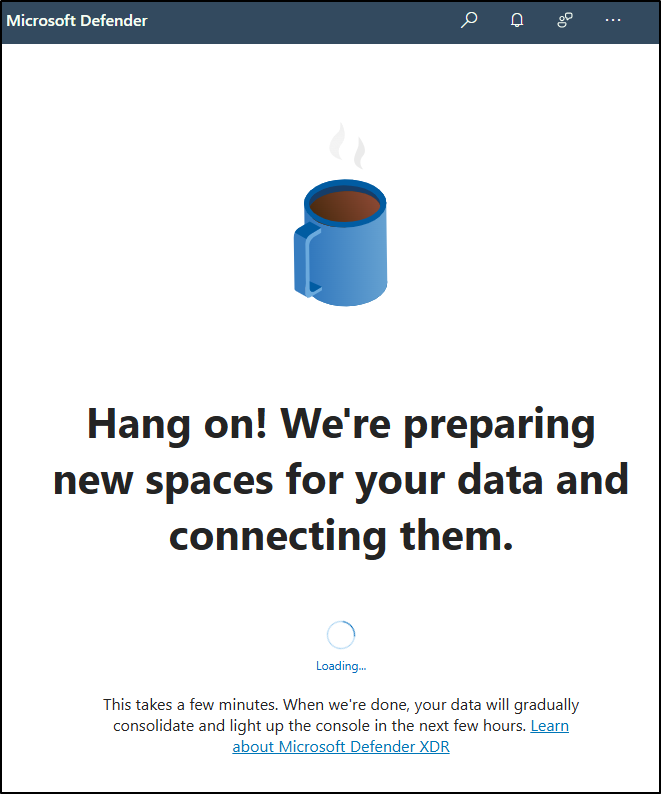
Microsoft Defender XDR is being initialized. You can continue with other tasks while it finishes setting up.
Task 5 – Configure multi-factor authentication in Microsoft Entra
In this task, you’ll configure multi-factor authentication (MFA) for the admin account to secure access to Microsoft Entra and other connected Microsoft 365 services.
-
In Microsoft Edge, navigate to
https://entra.microsoft.com/to open Microsoft Entra. -
On the Start by getting the app screen, install the Microsoft Authenticator app from your device’s app store, or open it if it’s already installed.
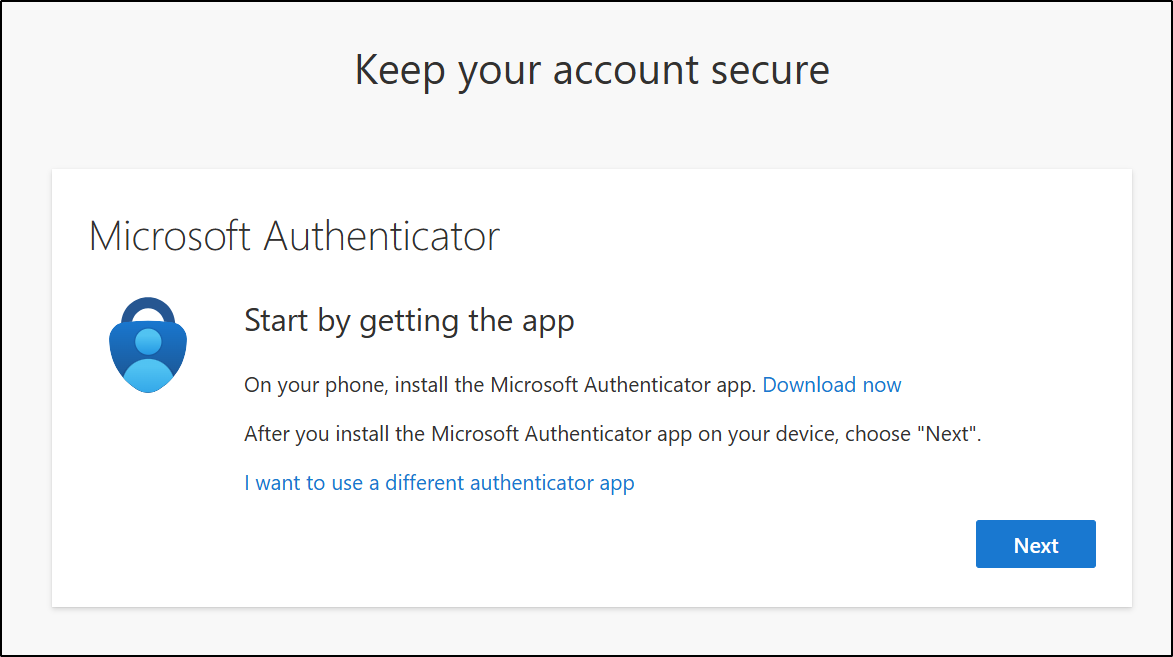
- If you prefer a different app, select I want to use a different authenticator app and follow the on-screen instructions.
-
Select Next.
-
On the Set up your account screen, follow the instructions on your phone to allow notifications, then select Next.
- If you already have the Microsoft Authenticator app installed and configured, you might not see this screen. In that case, continue to the next step.
-
On the Scan the QR code screen, use the Microsoft Authenticator app on your device to scan the QR code displayed on your screen, then select Next.
-
On your phone, approve the sign-in request by entering the number shown on your browser.
-
After approving the request, the Notification approved screen will appear. Select Next.
-
On the Success! screen, verify that your Default sign-in method shows Microsoft Authenticator, then select Done.
-
When prompted to sign in again, approve the sign-in request on your phone to verify your identity.
-
After the approval completes, you’ll be redirected to the Microsoft Entra admin center.
You’ve successfully configured and verified multi-factor authentication for the admin account in Microsoft Entra.