Lab 08 - Enable multi-factor authentication
Login type = Microsoft 365 + E5 tenant log-in
Lab scenario
To improve security in your organization, you’ve been directed to enable multifactor authentication for Microsoft Entra ID.
Estimated time: 15 minutes
IMPORTANT - A Microsoft Entra ID Premium license is required for this exercise.
Exercise 1 - Review and enable Multi-factor Authentication in Azure
Task 1 - Review Azure Multi-Factor Authentication options
-
Browse to the https://entra.microsoft.com and sign in using a Global administrator account for the directory.
-
Use the search feature and search for multifactor.
-
In the search results, select Multifactor authentication.
Alternatively, you can open Identity, then select Protection, and select Multifactor authentication.
-
On the Getting started page, under Configure, select Additional cloud-based MFA settings.
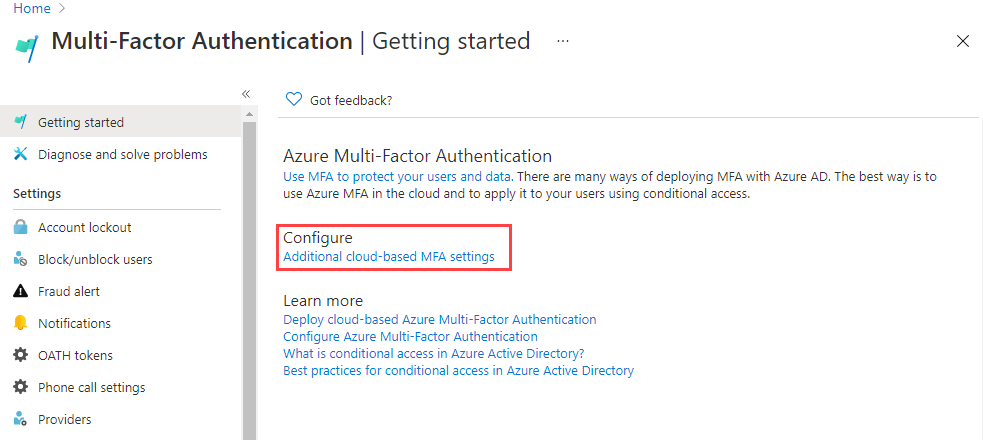
-
In the new browser page, you can see the MFA options for Azure users and service settings.
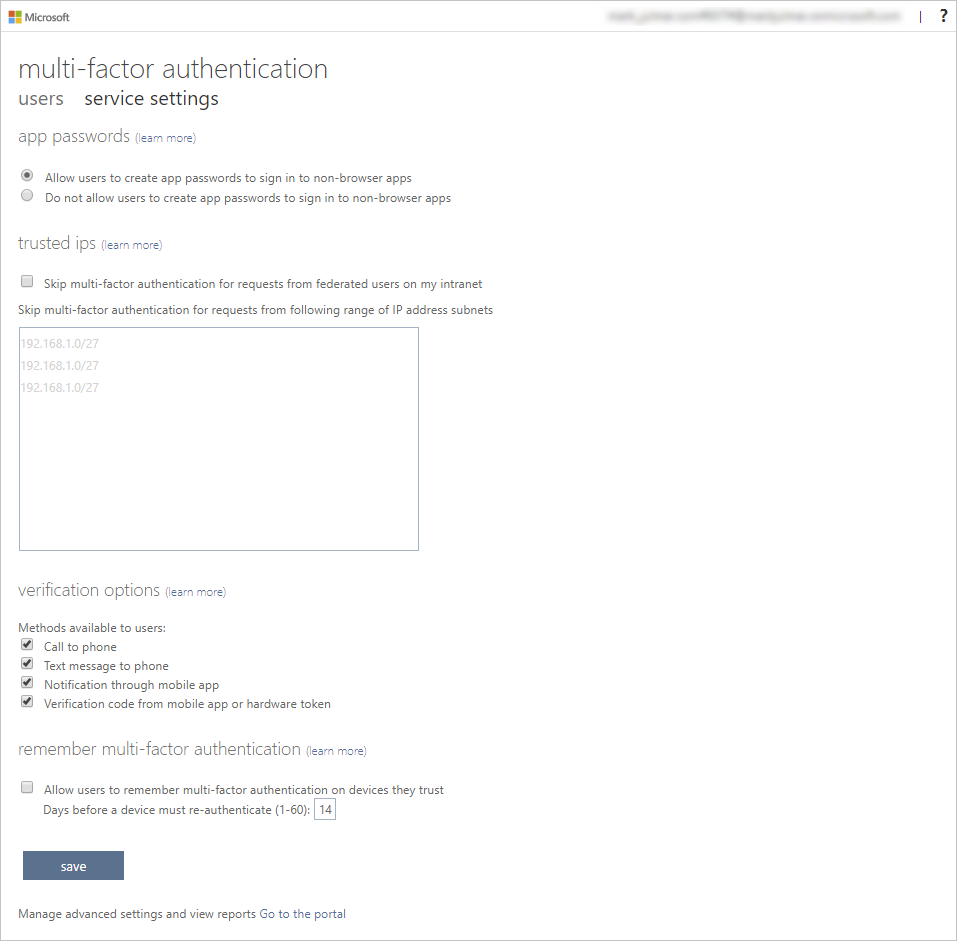
This is where you would select the supported authentication methods, in the screen above, all of them are selected.
You can also enable or disable app passwords here, which allow users to create unique account passwords for apps that don’t support multi-factor authentication. This feature lets the user authenticate with their Microsoft Entra identity using a different password specific to that app.
Task 2 - Setup conditional access rules for MFA for Delia Dennis
Next let’s examine how to set up Conditional Access policy rules that would enforce MFA for guest users accessing specific apps on your network.
-
Switch back to the Microsoft Entra admin center and select Identity, then Protection, and then Conditional access.
-
On the menu, Select + New policy. From the drop down select + Create new policy.
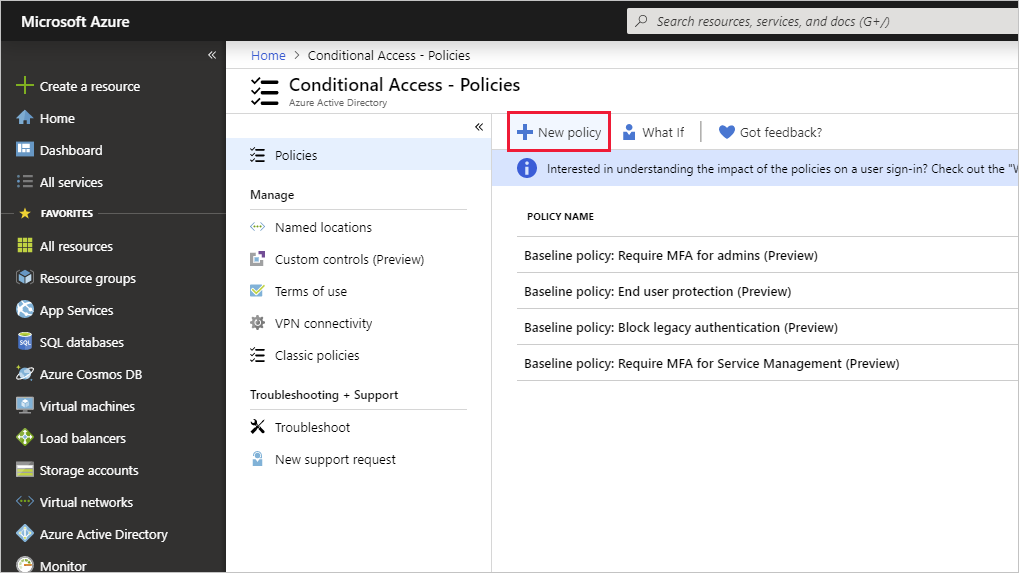
-
Name your policy, for example MFA_for_Delia.
-
Select Users or workload identities under Assignments.
- Select 0 users or workload identities selected
- On the right side screen, select Select users and groups check box to configure.
- Check Users and groups (available users will be populated to the right)
- Choose Delia Dennis from the list of users then choose Select button.
-
Select No target resources selected in Target resources.
- In the dropdown, make sure Cloud apps is selected.
- Under Include, mark Resources (formerly cloud apps) and note the warning the pops up about possibly locking yourself out.
- Now under Include section, choose the Select resources item.
- In the Select section select the None link.
- In the newly opened dialog, choose Office 365.
- Reminder - in a previous lab we gave Delia Dennis an Office 365 license and logged into ensure it worked.
- Choose Select.
-
Choose a network location in the Conditions section, then select Not configured.
- In the Conditions section choose the 0 conditions selected link.
- At the bottom of the newly opened menu find the Locations section, and select Not configured.
- Choose Yes for the Configure item.
- Select Any network or location.
-
Under Access Controls, find the Grant section and select the 0 controls selected link.
- Select the Require multifactor authentication check box to enforces MFA.
- Ensure that Require all the slected controls is selected.
- Select Select.
-
Set Enable policy to On.
-
Select the Create button to create the policy.
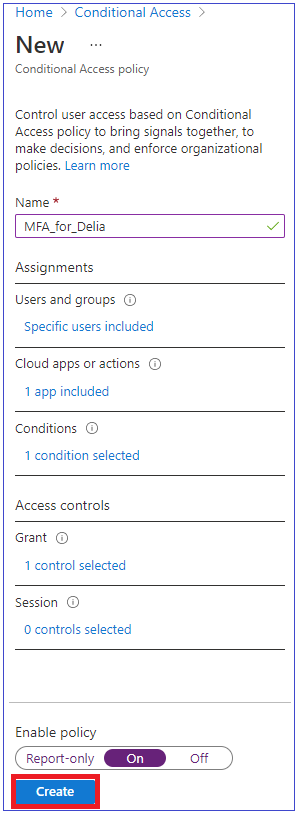
MFA is now enabled for your selected user and application(s). The next time a guest tries to sign into that app they will be prompted to register for MFA.
Task 3 - Test Delia’s login
- Open a new InPrivate Browsing windows.
- Connect to https://www.office.com.
- Select the sign-in option.
- Enter DeliaD@
<<your domain address>>. - Enter the password = Enter the Global admin password of the tenant (Note : Refer the ‘Lab Resources’ tab to retrieve the admin password).
Note - At this point one of two things will happen. You should get a message that you need to set up Authenticator app and register for MFA. Follow the prompts to complete using your personal phone. NOTE - there is a chance that you might get a login failure message with several options on how to proceed. Select the Try Again option in this case.
You can see that because of the Conditional Access rule we created for Delia, MFA is required to launch Office 365 home page.
Exercise 2 - Configure MFA to be required for login
Task 1 - Configure Microsoft Entra Per-User MFA
Finally, let’s look at how to configure MFA for user accounts. This is another way to get to the multi-factor auth settings.
-
Switch back to the Microsoft Entra admin center and find the Indentity left-hand navigation menu.
-
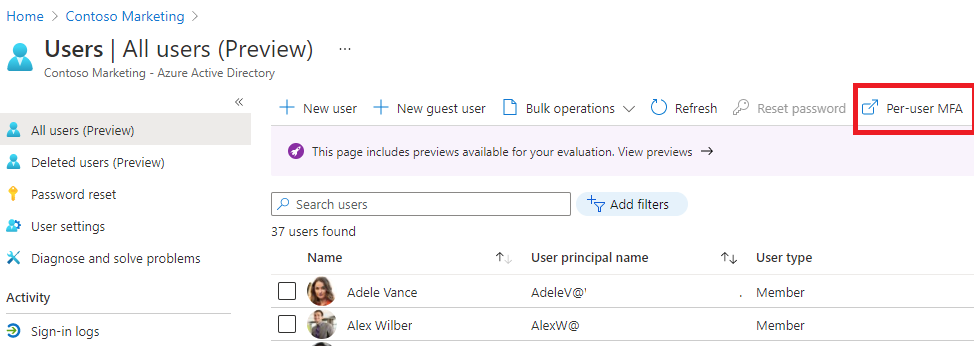
Select Users, then select All users.
- At the top of the Users pane, select Per-user MFA.
- NOTE: you may have to use the elipsis (…) to get to the Per-user MFA menu item.
-
A new browser tab/window will open with a multi-factor authentication user settings dialog.
You can enable or disable MFA on a user basis by selecting a user and then using the quick steps on the right side.
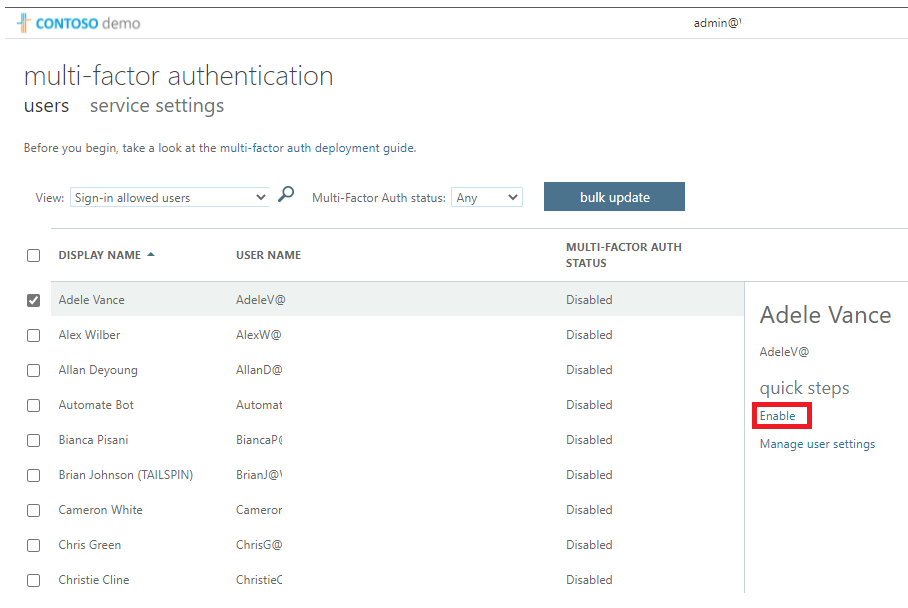
- Select Adele Vance with a check-mark.
- Select the Enable MFA option under quick steps.
- Read the notification popup if you get it, then select enable multi-factor auth button.
- Select Close.
- Notice that Adele now has Enabled as her MFA status.
- You can select service settings to see the MFA setting screen, seen earlier in the lab.
- Close the MFA setting tab.
Task 2 – Try logging in as Adele
- If you want to see another example of MFA login process, you can try to log in a Adele.