Learning Path 3 - Lab 1 - Exercise 1 - Enable Microsoft Defender for Cloud
Lab scenario
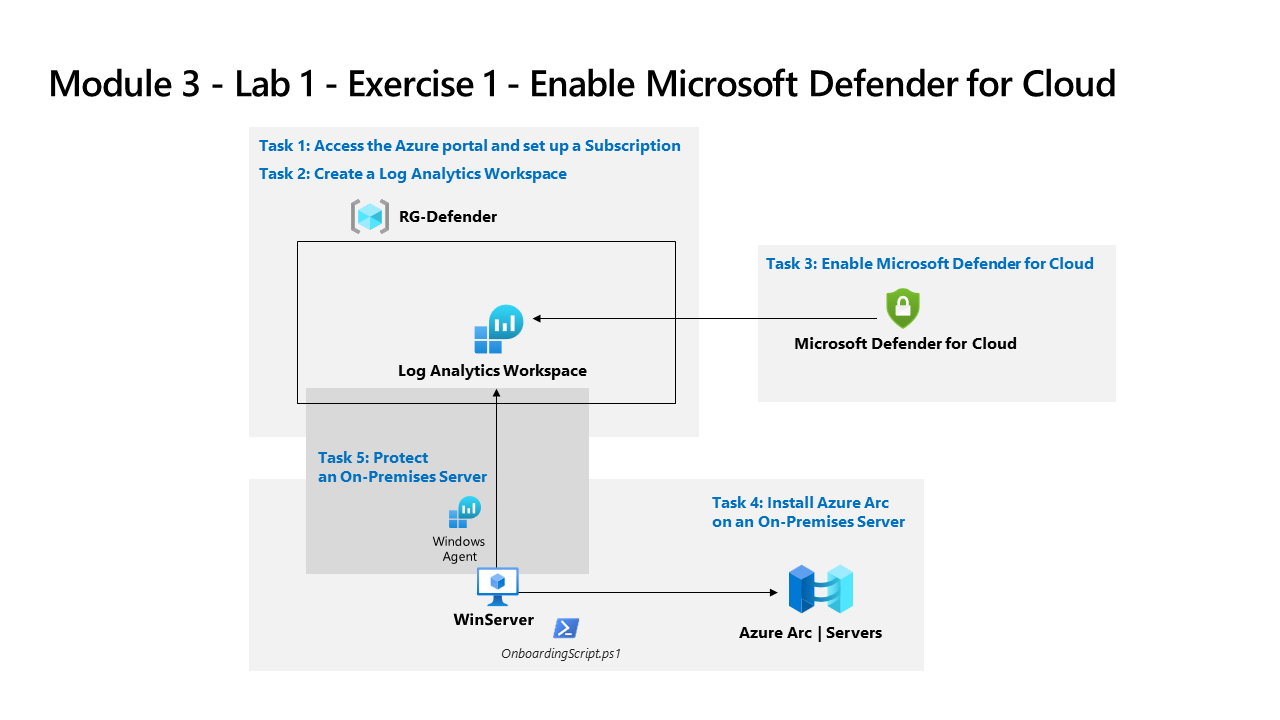
You’re a Security Operations Analyst working at a company that is implementing cloud workload protection with Microsoft Defender for Cloud. In this lab, you enable Microsoft Defender for Cloud.
Note: An interactive lab simulation is available that allows you to click through this lab at your own pace. You may find slight differences between the interactive simulation and the hosted lab, but the core concepts and ideas being demonstrated are the same.
Task 1: Access the Azure portal and set up a Subscription
In this task, you’ll set up an Azure Subscription required to complete this lab and future labs.
-
Log in to WIN1 virtual machine as Admin with the password: Pa55w.rd.
-
Open the Microsoft Edge browser or open a new tab if already open.
-
In the Microsoft Edge browser, navigate to the Azure portal at https://portal.azure.com.
-
In the Sign in dialog box, copy, and paste in the tenant Email account for the admin username provided by your lab hosting provider and then select Next.
-
In the Enter password dialog box, copy, and paste in the admin’s tenant password provided by your lab hosting provider and then select Sign in.
-
In the Search bar of the Azure portal, type Subscription, then select Subscriptions.
-
Select the “Azure Pass - Sponsorship” subscription shown (or equivalent name in your selected language).
Note: If the subscription is not shown, ask your instructor on how to create the Azure subscription with your tenant admin user credentials. Note: The subscription creation process could take up to 10 minutes.
-
Select Access control (IAM) and then select Add role assignment from the Grant access to this resource box.
-
Select the Privileged administrator roles tab and then select Owner. Select Next to continue.
-
Under the Members tab, select + Select members and select the MOD Administrator account and select Select to continue.
Note: If the Conditions tab displays a red dot, select Next, and either select Not constrained if presented with the Delegation type, or select Allow user to assign all roles (highly privileged) if presented with What user can do.
-
Select Review + assign twice to assign the owner role to your admin account.
Important: These labs have been designed to use less than USD $10 of Azure services during the class.
Task 2: Create a Log Analytics Workspace
In this task, you create a Log Analytics workspace for use with Azure Monitoring, Microsoft Sentinel and Microsoft Defender for Cloud.
-
In the Search bar of the Azure portal, type Log Analytics workspaces, then select the same service name.
-
Select +Create from the command bar.
-
Select Create new for the Resource group.
-
Enter RG-Defender and select Ok.
-
For the Name, enter something unique like: uniquenameDefender.
-
Select Review + Create.
-
Once the workspace validation has passed, select Create. Wait for the new workspace to be provisioned, this may take a few minutes.
Task 3: Enable Microsoft Defender for Cloud
In this task, you’ll enable and configure Microsoft Defender for Cloud.
-
In the Search bar of the Azure portal, type Defender, then select Microsoft Defender for Cloud.
-
On the Getting started page, under the Upgrade tab, make sure your subscription is selected, and then select the Upgrade button at the bottom of the page. Wait for the Trial started notification to appear, it takes about 2 minutes.
Hint: You can click the bell button on the top bar to review your Azure portal notifications.
Note: If you see the error “Could not start Azure Defender trial on the subscription”, continue with the next steps to enable all the Defender plans in Step 5.
-
In the left menu for Microsoft Defender for Cloud, under the Management, select Environment settings.
-
Select the “Azure Pass - Sponsorship” subscription (or equivalent name in your Language).
-
Review the Azure resources that are now protected with the Defender for Cloud plans.
Important: If all Defender plans are Off, select Enable all plans. Select the $200/month Microsoft Defender for APIs Plan 1 and then select Save. Select Save at the top of the page and wait for the “Defender plans (for your) subscription were saved successfully!” notifications to appear.
-
Select the Settings & monitoring tab from the Settings area (next to Save).
-
Review the monitoring extensions. It includes configurations for Virtual Machines, Containers, and Storage Accounts. Close the “Settings & monitoring” page by selecting the ‘X’ on the upper right of the page.
-
Close the settings page by selecting the ‘X’ on the upper right of the page to go back to the Environment settings and select the ‘>’ to the left of your subscription.
-
Select the Log analytics workspace you created earlier uniquenameDefender to review the available options and pricing.
-
Select Enable all plans (to the right of Select Defender plan) and then select Save. Wait for the “Microsoft Defender plan for workspace uniquenameDefender were saved successfully!” notification to appear.
Note: If the page is not being displayed, refresh your Edge browser and try again.
-
Close the Defender plans page by selecting the ‘X’ on the upper right of the page to go back to the Environment settings
Task 4: Install Azure Arc on an On-Premises Server
In this task, you install Azure Arc on an on-premises server to make onboarding easier.
Important: The next steps are done in a different machine than the one you were previously working. Look for the Virtual Machine name references.
-
Log in to WINServer virtual machine as Administrator with the password: Passw0rd! if necessary.
-
Open the Microsoft Edge browser and navigate to the Azure portal at https://portal.azure.com.
-
In the Sign in dialog box, copy, and paste in the Tenant Email account provided by your lab hosting provider and then select Next.
-
In the Enter password dialog box, copy, and paste in the Tenant Password provided by your lab hosting provider and then select Sign in.
-
In the Search bar of the Azure portal, type Arc, then select Azure Arc.
-
In the navigation pane under Azure Arc resources select Machines
-
Select + Add/Create, then select Add a machine.
-
Select Generate script from the “Add a single server” section.
-
In the Add a server with Azure Arc page, select the Resource group you created earlier under Project details. Hint: RG-Defender
Note: If you haven’t already created a resource group, open another tab and create the resource group and start over.
-
For Region, select (US) East Us from the drop-down list.
-
Review the Server details and Connectivity method options. Keep the default values and select Next to get to the Tags tab.
-
Review the default available tags. Select Next to get to the Download and run script tab.
-
Scroll down and select the Download button. Hint: if your browser blocks the download, take action in the browser to allow it. In Microsoft Edge Browser, select the ellipsis button (…) if needed and then select Keep.
-
Right-click the Windows Start button and select Windows PowerShell (Admin).
-
Enter Administrator for “Username” and Passw0rd! for “Password” if you get a UAC prompt.
-
Enter: cd C:\Users\Administrator\Downloads
Important: If you do not have this directory, most likely means that you are in the wrong machine. Go back to the beginning of Task 4 and change to WINServer and start over.
-
Type Set-ExecutionPolicy -ExecutionPolicy Unrestricted and press enter.
-
Enter A for Yes to All and press enter.
-
Type .\OnboardingScript.ps1 and press enter.
Important: If you get the error “The term .\OnboardingScript.ps1 is not recognized…“, make sure you are doing the steps for Task 4 in the WINServer virtual machine. Other issue might be that the name of the file changed due to multiple downloads, search for ”.\OnboardingScript (1).ps1” or other file numbers in the running directory.
-
Enter R to Run once and press enter (this may take a couple minutes).
-
The setup process opens a new Microsoft Edge browser tab to authenticate the Azure Arc agent. Select your admin account, wait for the message “Authentication complete” and then go back to the Windows PowerShell window.
-
When the installation finishes, go back to the Azure portal page where you downloaded the script and select Close. Close the Add servers with Azure Arc to go back to the Azure Arc Machines page.
-
Select Refresh until WINServer server name appears and the Status is Connected.
Note: This could take a couple of minutes.
Task 5: Protect an On-Premises Server
In this task, you manually install the Azure Monitor Agent by adding a Data Collection Rule (DCR) on the WINServer virtual machine.
-
Go to Microsoft Defender for Cloud and select the Getting Started page from the left menu.
-
Select the Get Started tab.
-
Scroll down and select Configure under the Add non-Azure servers section.
-
Select Upgrade next to the workspace you created earlier. This might take a few minutes. Wait until you see the notification “Microsoft Defender plan for workspace uniquenameDefender were saved successfully!”.
-
Select + Add Servers next to the workspace you created earlier.
-
Select Data Collection Rules
-
Select + Create.
-
Enter WINServer for Rule Name.
-
Select your Azure Pass - Sponsorship subscription and select a Resource Group. Hint: RG-Defender
-
You can keep the default East US region or select another preferable location.
-
Select the Windows radio button for Platform Type and select Next: Resources.
-
In the Resources tab, + Add resources.
-
In the Select a scope page, expand the Scope column for RG-Defender (or the Resource Group your created), then select WINServer and select Apply.
Note: You may need to set the column filter for Resource type to Server-Azure Arc if WINServer is not displayed.
-
Select Next: Collect and deliver
-
In the Collect and deliver tab, select + Add data source
-
In the Add a data source page, select Performance Counters from Data source type.
Note: For the purposes of this lab you could select Windows Event Logs. These selections can be revised later.
-
Select the Destination tab
-
Select Azure Monitor Logs in the Destination Type dropdown
-
Select your Azure Pass - Sponsorship subscription from the Subscription dropdown
-
Select your workspace name Hint: RG-Defender from the Account or namespace dropdown
-
Select Add data source and select Review + create
-
Select Create after Validation passed is displayed.
-
The Data Collection Rule creation initiates the installation of the AzureMonitorWindowsAgent extension on WINServer.
-
When the Data Collection Rule creation completes, enter WINServer in the Search resources, services and docs search bar, and select WINServer from Resources.
-
On WINServer scroll down through the left menu to Settings and Extensions.
-
The AzureMonitorWindowsAgent should be listed with a Status of Succeeded.
-
You can move on to the next lab and return later to review the Inventory section of Microsoft Defender for Cloud to verify that WINServer is included.