Note: This lab builds on Lab 01 and Lab 02. To complete this lab, you will need an Azure subscription. in which you have administrative access.
General guidelines
- When creating objects, use the default settings unless there are requirements that require different configurations.
- Only create, delete, or modify objects to achieve the stated requirements. Unnecessary changes to the environment may adversely affect your final score.
- If there are multiple approaches to achieving a goal, always choose the approach the requires the least amount of administrative effort.
We need to configure Microsoft Sentinel to receive security events from virtual machines that run Windows.
Architecture diagram
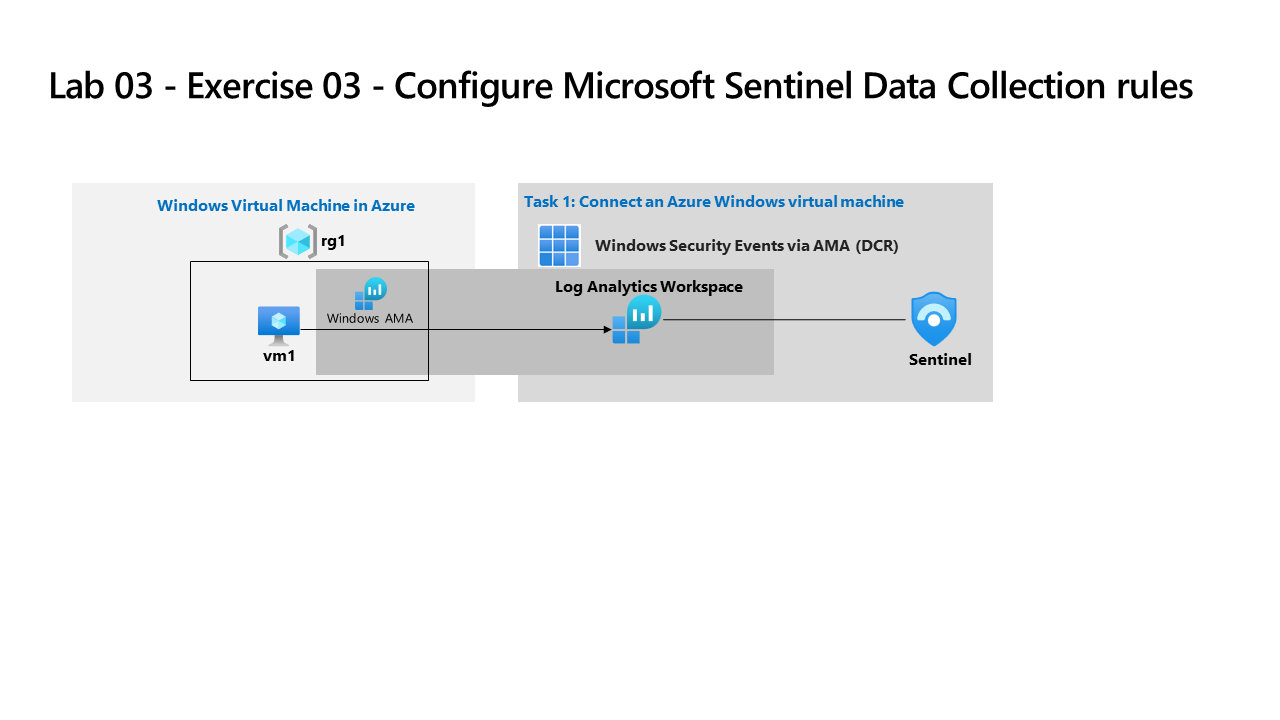
Skilling tasks
You need to validate the Microsoft Sentinel deployment to meet the following requirements:
- Configure the Windows Security Events via AMA connector to collect all security events from only a virtual machine named VM1.
- Create a near-real-time (NRT) query rule to generate an incident based on the following query.
SecurityEvent
| where EventID == 4732
| where TargetAccount == "Builtin\\Administrators"
- Create an automation rule that assigns Operator1 the Owner role for incidents that are generate by the NRT rule.
Exercise instructions
Note: In the following tasks, to access
Microsoft Sentinel, select theworkspaceyou created in Lab 01.
Task 1 - Configure Data Collection rules (DCRs) in Microsoft Sentinel
Configure a Windows Security Events via AMA connector. Learn more about Windows Security Events via AMA connector.
- In
Microsoft Sentinel, go to theConfigurationmenu section and select Data connectors - Search for and select Windows Security Events via AMA
- Select Open connector page
- In the
Configurationarea, select +Create data collection rule - On the
Basicstab enter aRule Name - On the
Resourcestab expand your subscription and theRG1resource group in theScopecolumn - Select
VM1, and then select Next: Collect > - On the
Collecttab leave the default ofAll Security Events - Select Next: Review + create >, then select Create
Task 2 - Create a near real-time (NRT) query detection
Detect threats with near-real-time (NRT) analytic rules in Microsoft Sentinel. Learn more about NRT Analytic rules in Microsoft Sentinel.
- In
Microsoft Sentinel, go to theConfigurationmenu section and select Analytics - Select + Create, and NRT query rule (Preview)
- Enter a
Namefor the rule, and select Privilege Escalation fromTactics and techniques. - Select Next: Set rule logic >
-
Enter the KQL query into the
Rule queryformSecurityEvent | where EventID == 4732 | where TargetAccount == "Builtin\\Administrators" - Select Next: Incident settings >, and select Next: Automated response >
- Select Next: Review + Create
- When validation is complete select Save
Task 3 - Configure automation in Microsoft Sentinel
Configure automation in Microsoft Sentinel. Learn more about Create and use Microsoft Sentinel automation rules.
- In
Microsoft Sentinel, go to theConfigurationmenu section and select Automation - Select + Create, and Automation rule
- Enter an
Automation rule name, and select Assign owner fromActions - Assign Operator1 as the owner.
- Select Apply